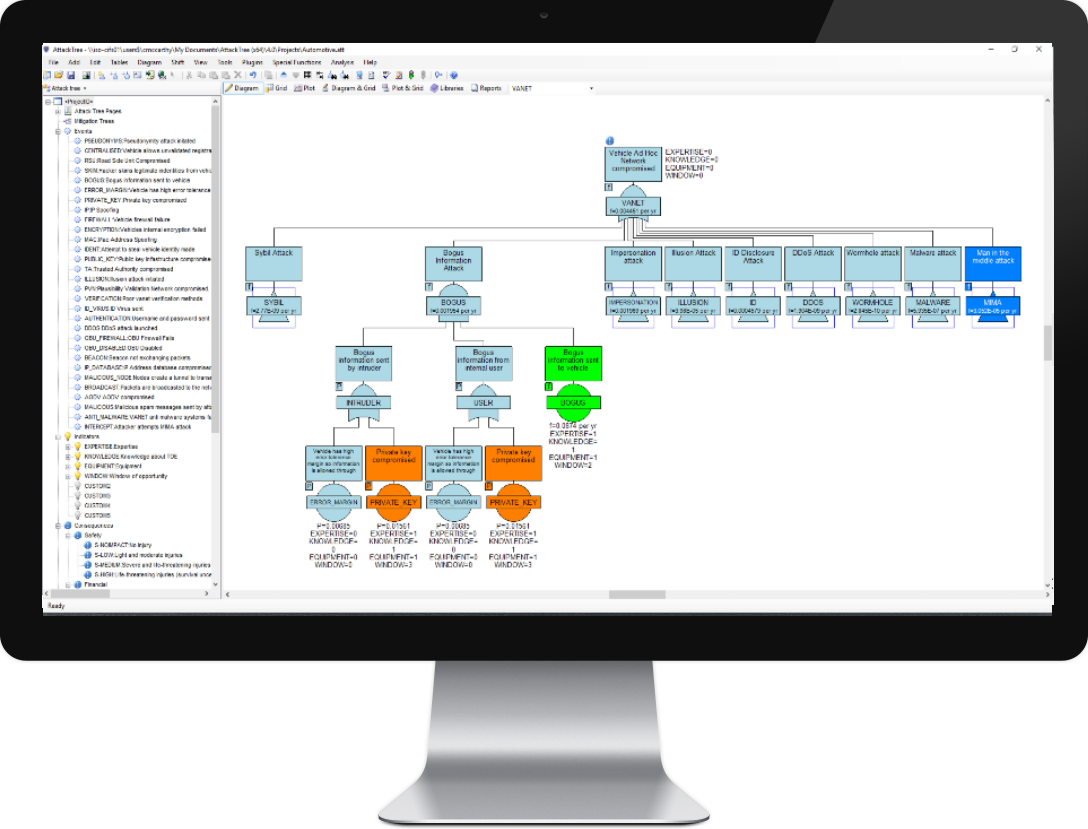
AttackTree
Model system vulnerability, identify weakspots and improve security using threat analysis and attack trees. Construct graphical representations of measures designed to reduce the consequences of a successful attack with mitigation trees.
- Analyze threats according to standards such as ISO 26262, ISO/SAE 21434, J3061, DO-356 and ED-203
- Identify where your system is vulnerable to an attack
- Improve the security of your assets and IT systems
- Model consequence mitigation
- Build models quickly using the advanced GUI features of AttackTree
- Link to Requirements Management tools such as Jama Connect®
Our software has been in continuous development since the 1980s and is the recognized standard for safety and reliability professionals.
Why choose AttackTree
There are many reasons to choose AttackTree – here are
just a few:
Consequence Driven AttackTrees
Threat Analysis and Risk Assessment
ISO 21434, SAE J3061 and ISO 26262
Read More On Cyber Security Analysis
Read More On Threat Analysis
Mitigation Trees
Our Credentials
Isograph's software is used in over 1900 companies, across 12,000 sites in 75 countries. We're ISO-9001 certified. We have software certifications with SAP and are IBM Business
Partners.
Premium Support
With support engineers located in the United Kingdom and the United States with same day response times our support is second to none.
Industry Standards
Our software complies with recognised standards, including but not limited to ISO 26262, IEC 61508, AIAG & VDA, ISO 21434, ARP 4761, SN29500, IEC 61709, FIDES, DO-356 and ED-203.
Development
Our software has been in continuous development since 1986 with upgrades and features driven by users and industry standards.